The Spectre and Meltdown security stories were the major focus of the week. While both flaws are serious, Spectre hits everyone, while Intel is the company principally exposed by Meltdown. Meltdown is also the flaw associated with early reports of performance losses in some web servers and virtualization workloads, though it’s still not at all clear what kind of real-world penalties we should be expecting. Nevertheless, lawsuits are already starting to pile up, and there’s a lot of discussion over CEO Brian Krzanich’s recent stock sale.
Intel’s initial response to Meltdown was a masterful example of corporate doublespeak. It opens by noting Intel doesn’t believe the exploit can be used “to corrupt, modify, or delete data,” even though that’s literally not the problem being discussed. Meltdown allows data to be read out of kernel memory; it doesn’t let the attacker write it. Intel doesn’t distinguish between Meltdown and Spectre, and it name-checks AMD and ARM as a way of making the risk profile of the situation seem more evenly distributed than it appears to be. If Intel was hoping to avoid lawsuits, however, it hasn’t worked. As Gizmodo details, three separate class action suits have been filed against the company already.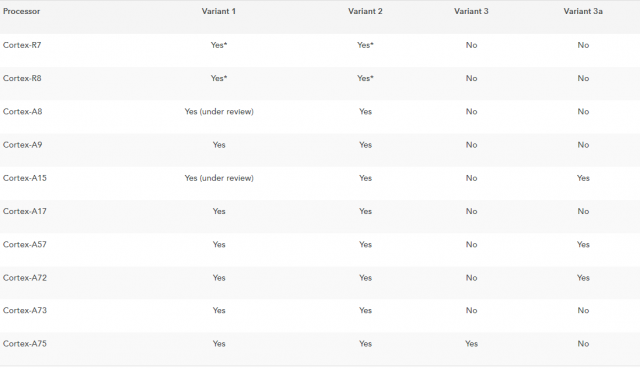
ARM defines its own 3a variant of meltdown but doesn’t believe a software fix is required. Only the Cortex-A75 is affected by Meltdown (Variant 3).
What’s less clear is whether these lawsuits have any meaningful reason to exist. They’ve all been filed on behalf of consumers on the basis of lost performance, but we don’t have any information yet showing that consumer applications are impacted by Meltdown or Spectre. Until that’s proven, the lawsuit standing seems a tad weak.
Intel CEO Brian Krzanich’s actions, however, could still spell some trouble for the CPU giant. On October 30, months after being informed of the Meltdown and Spectre security flaws, Krzanich announced he would liquidate some 245,000 shares of Intel stock. He currently holds 250,000 shares, the minimum he’s required to hold as company CEO. All told, he sold $50 million worth of stock at the tail end of the year, just before news of these bugs began to break. The SEC could choose to investigate the situation — it launched an investigation of suspiciously timed stock sales in the Equifax breach this year — but no announcements have been made yet.
But while Intel’s handling of its PR response to this set of flaws deserves criticism, the security flaws themselves will be difficult to pin on negligence. Speculative processing and out-of-order execution have been critical components of high-end CPU performance for decades. Intel may be uniquely exposed to Meltdown, but Spectre hits everyone precisely because it weaponizes functional characteristics in a way that wasn’t done before. It’s hard to argue that a company was negligent in its designs when no one had previously identified an attack vector to protect against, or created even a proof-of-concept to expose the issue.
No comments:
Post a Comment