Nearly every web browser now comes with a password manager tool, a lightweight version of the same service offered by plugins like LastPass and 1Password. But according to new research from Princeton"s Center for Information Technology Policy, those same managers are being exploited as a way to track users from site to site.
The researchers examined two different scripts — AdThink and OnAudience — both of are designed to get identifiable information out of browser-based password managers. The scripts work by injecting invisible login forms in the background of the webpage and scooping up whatever the browsers autofill into the available slots. That information can then be used as a persistent ID to track users from page to page, a potentially valuable tool in targeting advertising.
The plugins focus largely on the usernames, but according to the researchers, there’s no technical measure to stop scripts from collecting passwords the same way. The only robust fix would be to change how password managers work, requiring more explicit approval before submitting information. “It won"t be easy to fix, but it"s worth doing,” says Arvind Narayanan, a Princeton computer science professor who worked on the project.
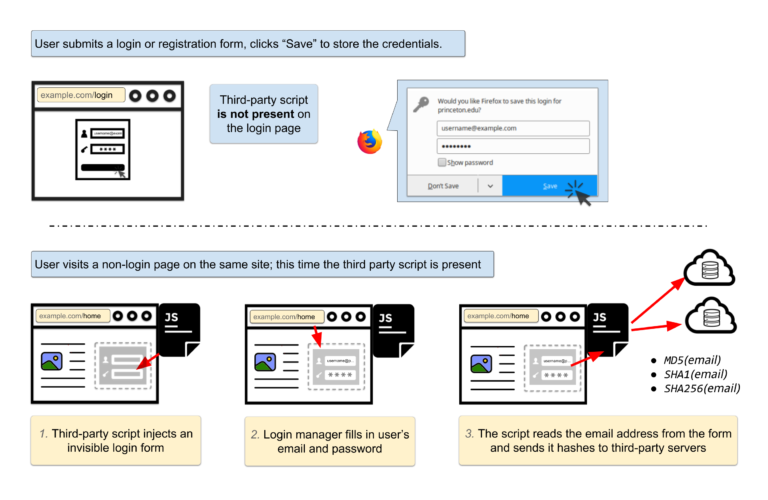
In the case of AdThink, that information was also being funneled back to Axciom, a massive consumer data broker, presumably to be added to the growing file on whoever was visiting the site. AudienceInsights, which operates AdThink, lets users see their unique user ID for the system and attempt to opt out, although it’s unclear how robust that opt-out truly is. Audience Insights did not respond to a request for comment.
For Narayanan, most of the blame goes to the websites who choose to run scripts like AdThink, often without realizing how invasive they truly are. “We"d like to see publishers exercise better control over third parties on their sites,” Narayanan says. “These problems arise partly because website operators have been lax in allowing third-party scripts on their sites without understanding the implications.”
No comments:
Post a Comment